
Picture this: a fault-tolerant quantum computer boots up and every RSA or ECC key online shatters in milliseconds. Security leaders call that instant “Q-Day,” and conservative roadmaps place it before January 1, 2030. Attackers aren’t waiting—they’re siphoning encrypted traffic now, planning to replay it once quantum decryption lands. We need post-quantum cryptography in production long before that countdown hits zero, and a new guard of startups is sprinting to deliver it.
Why startups hold the keys
Large vendors set standards but change slowly, like cargo ships turning in deep water. Startups pivot in weeks, not quarters, and that agility matters when each month shortens the runway to Q-Day.
For this report we selected ten companies that satisfy five strict tests: sizable funding rounds, patented innovation, early customer deployments, alignment with NIST or ETSI guidance, and impact that reaches beyond a single niche.
These filters remove hype and spotlight builders already defending fighter-jet telemetry, crypto wallets, and 5G handsets. Together they span the full stack—from lattice-based post-quantum cryptography and quantum-grade randomness to key orchestration and satellite links.
Treat the list as a menu for your own upgrade path. Whether you secure cloud APIs, field sensors, or long-haul fiber, at least one of these startups offers a pilot you can launch this quarter.
Next, we explore the code-crunching side of the story and meet three teams rewriting the mathematics behind modern encryption.
PQShield: re-coding the math itself
Oxford-based PQShield replaces brittle RSA with lattice-based post-quantum cryptography baked directly into silicon. In February 2024 the team closed a $37 million Series B led by Addition and Chevron Technology Ventures, calling it a “commercial imperative” for quantum-safe security (PQShield press release).
Money is only half the story. PQShield engineers co-authored several NIST finalist algorithms and demonstrated that they run efficiently on real hardware. Their secure co-processor IP integrates with Arm and RISC-V designs, protecting everything from payment cards to car ECUs without a costly parts swap. On the software side, drop-in libraries let cloud apps negotiate quantum-safe TLS in minutes.
The takeaway: if you rely on embedded devices—or ship code that lands on them—PQShield offers a practical path to harden millions of endpoints before quantum attackers arrive.
CryptoNext Security: a bridge for every legacy system
Paris-based CryptoNext skips shiny new protocols and tackles the mess you already own—decades of RSA certificates, embedded firmware, and forgotten VPN boxes. Its Quantum Safe Remediation suite scans that sprawl, flags weak links, and swaps in lattice- or hash-based post-quantum cryptography with only a brief service pause.
The approach attracted €11 million in funding from AXA Venture Partners and Quantonation. More importantly, it earned pilot runs inside European banks where downtime is not an option. In one test, a trading link shifted from classical TLS to a hybrid post-quantum mode during live market hours without losing a single packet.
If your roadmap says “migrate over the next ten years,” CryptoNext compresses that to one quarter. The platform turns crypto-inventory and key rotation into a guided checklist so your team can focus on policy instead of packet captures.
Project Eleven: immunizing blockchains before hackers cash out
Cryptocurrency wallets rely on elliptic-curve signatures, a prime target for quantum computers, so Project Eleven, founded in California in 2022, reinforces the wallet layer with Post-Quantum Cryptography built around an ML-KEM-over-WebSockets handshake that remains private even if today’s TLS is cracked after Q-Day.
Its Yellowpages registry lets Bitcoin holders post a quantum-safe proof of ownership today. Project 11’s public risk dashboard counts 6 262 905 bitcoins—about US$648 billion on January 17 2025—sitting in addresses whose public keys are already exposed, making them prime quantum targets. Even if a quantum thief steals the original keys later, the chain still records who owned the coins first. Custody providers are already piloting the service to protect an estimated $600 billion in assets.
Powered by $6 million in seed funding from Variant and Quantonation, the team ships quickly. Core contributors came from Coinbase and university cryptography labs; they publish audits in the open and sponsor academic research to keep the math peer-reviewed.
For anyone managing digital assets, Project Eleven offers a painless first step: publish a quantum-safe fallback now and sleep better tonight.
QuSecure: turning complex upgrades into a one-click policy
Most enterprises don’t fear quantum math, they fear forklift upgrades. QuSecure solves that problem. Its QuProtect platform sits in the network path and swaps fragile RSA keys for post-quantum cryptography without touching endpoints.
That promise led to a Phase III contract with the United States Air Force, proving the software on live defense networks where downtime is unacceptable. Administrators feed QuProtect a simple policy such as “use hybrid TLS externally, classical internally,” and the middleware handles key generation, certificate lifecycles, and graceful fallback if a peer lags.
Because everything runs in software, pilots spin up fast. One government test launched a quantum-safe VPN from California to Washington, D.C. in an afternoon. For teams that manage tens of thousands of links, QuSecure offers the goal everyone wants: quantum readiness you enable like a feature flag, not a forklift.
QuintessenceLabs: randomness at gigabit speed
Encryption is only as strong as the dice you roll. Most systems simulate randomness with algorithms that a future quantum attacker could predict. QuintessenceLabs fixes that gap. Its qStream appliance generates quantum-random bits at 10 Gbps, giving key management services true entropy for post-quantum cryptography.

Enterprises install the box in a rack, point existing key servers at its API, and every symmetric key, password reset token, or one-time pad draws on laser-grade randomness. Pair qStream with the QLock key manager and you gain policy controls, audit trails, and automated rollovers, all fueled by quantum noise.
Australian defense agencies already use the combination to protect classified stores. Banks lean on it when regulators demand proof that keys are never reused. If you worry about tomorrow’s math, start by fixing today’s randomness. QuintessenceLabs makes that upgrade as easy as plugging in a new power cord.
Crypto Quantique: unique keys born inside every chip
Most IoT devices store secrets in flash memory. A determined attacker with a soldering iron can read those bits in minutes. Crypto Quantique rewrites that model. Its QDID intellectual property measures quantum-tunneling variations in each transistor and recreates a 256-bit key on every boot, so nothing sits in memory for an oscilloscope to capture.
Developers pair this hardware root with QuarkLink, a cloud service that auto-enrols tens of thousands of sensors to AWS or Azure in a single step. Deployments that once needed secure rooms and laser-etched labels now happen on the factory line.
If physics cannot be cloned, the key cannot be cloned. For smart meters, medical implants, and autonomous vehicles that must remain secure for decades of post-quantum cryptography threats, Crypto Quantique delivers a hardware anchor attackers cannot counterfeit.
Qrypt: secret keys that never cross the wire
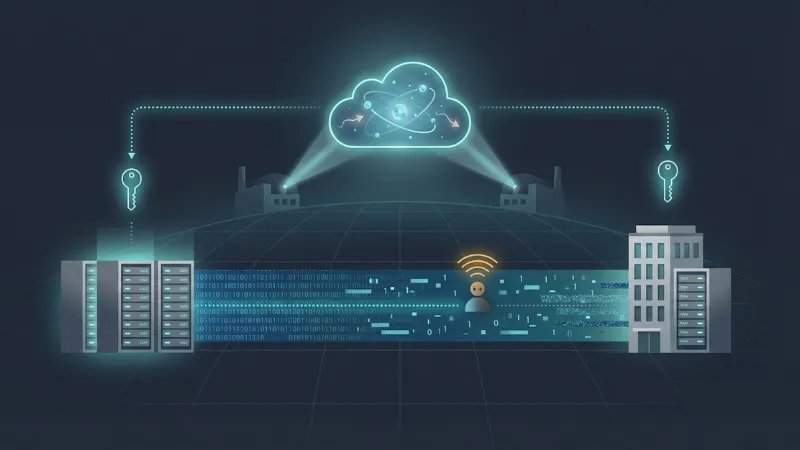
Traditional encryption sends a key wrapped in another key and hopes no one records the traffic. Qrypt removes that risk. Both endpoints pull quantum-grade randomness from the company’s cloud service and independently derive the same one-time key, so nothing travels over the network.
The raw entropy comes from photon-based random generators licensed from Oak Ridge and Los Alamos National Laboratories. A distributed-key algorithm stitches those random bits into matching secrets on each side, leaving eavesdroppers with useless noise.
Financial firms use the service to encrypt backups that must stay confidential for decades, while telecom operators test it as a software-only alternative to heavy quantum-key-distribution hardware. For teams that need post-quantum cryptography today but cannot run new fiber or launch satellites, Qrypt offers a pragmatic path: add an SDK, call an API, and keep keys off the wire.
ID Quantique: two decades ahead on quantum links
Founded in Geneva in 2001, ID Quantique shipped the first commercial quantum-key-distribution box when most of us still used dial-up. Today its Cerberis platform pushes single photons through ordinary fiber, refreshing encryption keys thousands of times per second so any tap shows up as measurable noise.

Telecom giant SK Telecom invested $65 million to weave the technology into South Korea’s 5G backbone. European banks use the same gear to secure inter-data-center links, while Samsung added IDQ’s quantum-random chip to flagship smartphones, strengthening mobile payments with post-quantum cryptography.
For workloads that demand absolute assurance—national elections, grid control, sovereign data vaults—ID Quantique offers battle-tested hardware and more than twenty years of field lessons.
QNu Labs: India’s home-grown quantum backbone
Covering a country the size of India with fiber is hard. Securing that reach against a future quantum adversary is harder. Bengaluru-based QNu Labs rises to both challenges, building quantum-key-distribution boxes rugged enough for dusty data centers and affordable for telecom budgets.
The company’s Tropos system already carried quantum keys between defense sites in New Delhi and Mumbai. In April 2025, India’s National Quantum Mission invested ₹580 million (about $7 million) to accelerate domestic production. QNu pairs Tropos with Hodos, a key-management layer that injects fresh quantum keys straight into everyday VPN routers.
Banks testing the stack say integration feels like adding a new certificate authority, not a moon-shot project. For operators working in demanding geographies, QNu Labs proves that post-quantum cryptography can be built, deployed, and supported entirely in-country on timelines that match ambitious digital-inclusion goals.
SpeQtral: quantum keys from low-Earth orbit
Fiber can reach only so far before losses kill a quantum signal. Singapore-based SpeQtral sidesteps that limit by lifting the link into space. The startup, spun out of the Centre for Quantum Technologies, is building suitcase-size satellites that beam entangled photons to ground stations thousands of kilometres apart.

In March 2021 it raised $8.3 million in seed funding from Temasek’s deep-tech arm to flight-qualify the optics. The mission profile is straightforward: pass overhead, deliver fresh keys, move on. Banks, maritime operators, and remote research bases will reserve downlink windows the same way they book earth-observation imagery.
Balloon and drone tests have shown the hardware survives vibration, temperature swings, and bright daylight. A government-funded launch is on the manifest, aiming to create Asia’s first commercial space-based post-quantum cryptography service. When that small satellite unfurls its solar panels, global key exchange will no longer depend on submarine cables; it will ride a column of starlight.
Conclusion
Seeing ten breakthrough demos is exciting; turning them into a rollout plan keeps you employed. Start with three moves you can launch this quarter.

First, inventory every place your stack still relies on RSA or ECC. Web servers are obvious, but buried firmware, printer queues, and archived backup tapes count too. Tools from CryptoNext or QuSecure crawl that maze in hours, not months, and hand you a colour-coded risk list.
Second, inject quantum-grade randomness. Whether you install a rack-mounted qStream box or call Qrypt’s cloud API, stronger entropy is a drop-in upgrade that raises security across the board. Keys last longer when they start stronger.
Third, pilot at least one fresh key-delivery method such as hybrid post-quantum TLS for cloud apps, a fibre QKD link for a high-value data-centre pair, or a Yellowpages proof for digital assets. The goal is not perfection; it is organisational muscle memory. Once playbooks exist, scaling becomes a budgeting exercise rather than an R&D scramble.
Pick the slice that protects your highest-value data and move it onto a quantum-safe rail. Every migration milestone you hit now is a breach you will never have to report later.





